What makes this botnet special?
What is it?
Meris, a recently emerging variant of botnet, has given the Internet a not-so-gentle reminder that DDoS attacks are not a thing of the past. During the month of June 2021, the presence of this new botnet was picked up by QRator. Since then, it has continuously grown to what is now an estimated size of 250,000 infected hosts. These hosts have been identified as MikroTik routers, with the vendor noting that a RouterOS vulnerability patched in 2018 is being used to compromise said devices.

What makes this botnet special?
The majority of DDoS rely on volumetric attacks to saturate their target with a large amount of bandwidth. This is true for many reasons, with the first being that the cost of launching such attacks is less expensive. Most of this traffic is sent over UDP, a protocol that allows for the immediate transmission of data without the need to establish a connection with the other host. For malicious actors, this means that less work is required to orchestrate the same size of attack. With TCP, a protocol commonly used for web-servers and other applications which require reliable transport of data, a three-way handshake is required before the client is able to send any information. Additionally, the size of a TCP header is anywhere between 20 to 60 bytes, whereas UDP packets always carry a fixed 8-byte header. This added overhead which reduces throughput along with the need to exchange packets beforehand typically deters the typical attacker. With IoT devices typically having low-grade hardware, the botnet relies on the combined network usage of its slaves to overwhelm the target as opposed to their processing capabilities.

So far, reports of attacks from the Meris botnet describe high-rate HTTP requests. In August, Cloudflare published an article which detailed a 17.2 M rps DDoS attack. Not only does Meris target TCP based services, but the infected devices connect to the target and then pipeline multiple HTTP requests to increase their throughput. We can nonetheless see that while this attack is very much high-rps and easily capable of saturating servers solely based on the number of connections that they can handle at any given moment, it still tries to deliver bandwidth in as large of a volume as manageable, therefore making this attack capable of overwhelming both system resources like CPU and memory while also clogging the network. With the constant expansion of web services, it’s likely that the individuals behind this botnet are putting focus on L7 attacks. For the majority of DDoS mitigation providers, most of which only provide L4 filtering capabilities, it is unlikely that the current solutions they have in place for DDoS will suffice. Fortunately, Core Technology has recently made an HTTPS filter available which sits in front of the customer’s website and ensures that only legitimate HTTP requests are being received by the web-server. As the company grows exponentially, the number of services offered increases at the same rate to ensure that we are always one step ahead.
Influences on DDoS trends
It is possible that Meris will continue to get worse before it improves. As outlined by MikroTik, the chances of the already-compromised routers being recovered is unlikely.
Unfortunately, closing the vulnerability does not immediately protect these routers. If somebody got your password in 2018, just an upgrade will not help. You must also change password, re-check your firewall if it does not allow remote access to unknown parties, and look for scripts that you did not create.
We have tried to reach all users of RouterOS about this, but many of them have never been in contact with MikroTik and are not actively monitoring their devices. We are working on other solutions too.
Whether or not these devices continue to collectively operate as a source of DDoS attacks is dependent on tech-savvy customers going out of their way to pick up on the issue and then regain control over their MikroTik router. With nearly all infected devices being used in DDoS attacks being the result of misconfigured, outdated, or neglected software running on systems, it’s unlikely that there will be a sudden turnaround when it comes to Meris.
Furthermore, with Meris making headlines, it’s possible that other like-minded criminals will follow this trend of attack vectors being used. As a result, more widespread DDoS attacks may end up targeting web applications instead. Despite this, there is nonetheless no shortage in volumetric UDP floods. Just over the past week, Core Technology has seen a myriad of attacks exceeding 1 Tbps on a daily basis.
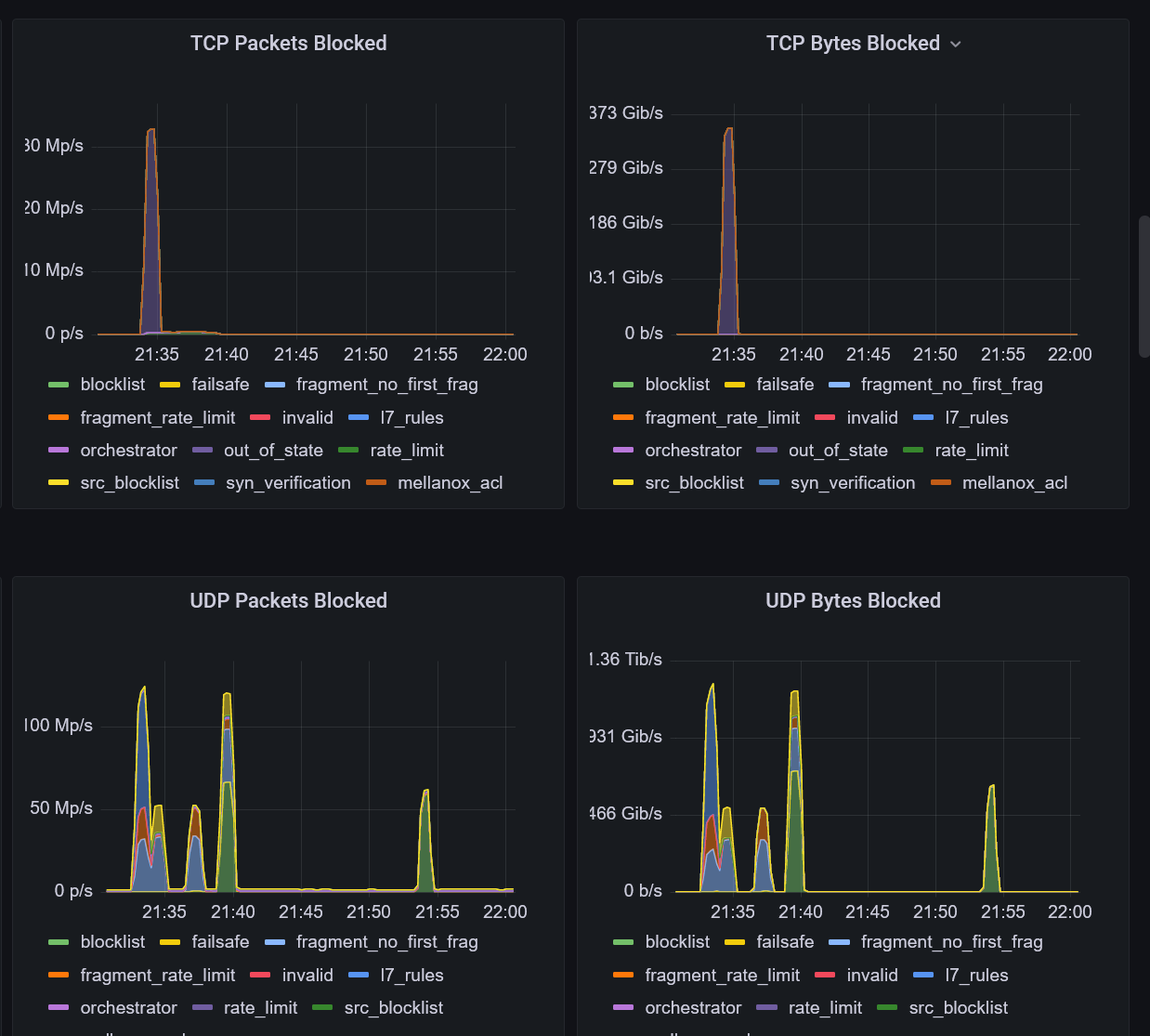
We can distinguish several bursts of high-bandwidth attacks in the graphs above. Out of the 1.2 Tbps DDoS, roughly 350 Gbps of it was composed of TCP-based attacks.
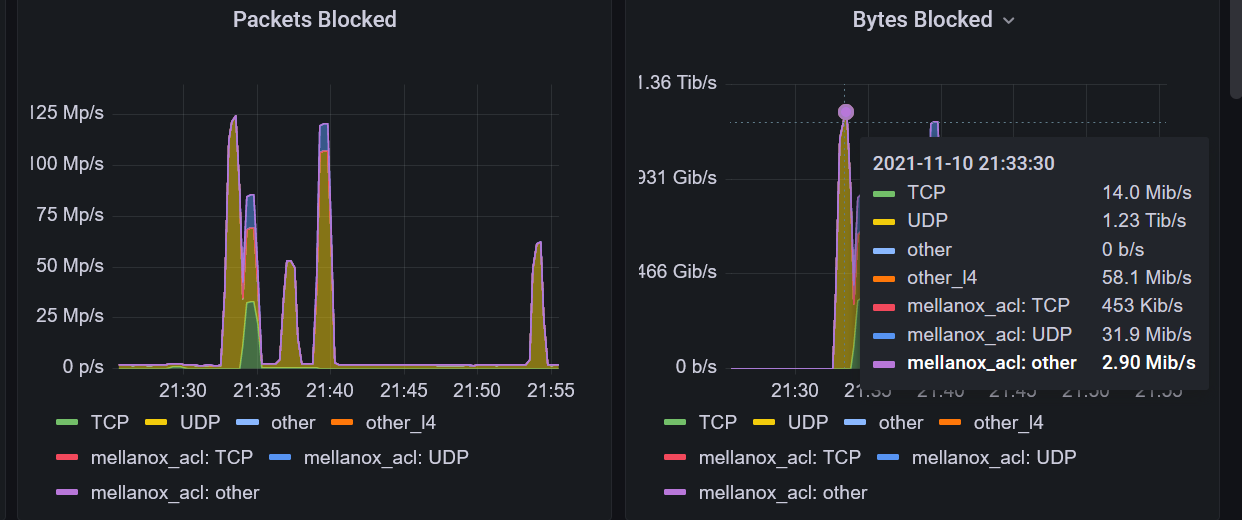
On the other hand, another brief spike in DDoS traffic during the same timeframe was observed to be solely 1.23 Tbps of UDP traffic. Further inspection revealed that this was another reflected DNS attack. Despite the Internet attempting to reduce the impact of DNS amplification by deprecating the ANY query type, we are faced with merely more proof that there is still a significant amount of misconfigured DNS servers on the Internet which are being leveraged.
Resolutions
While there may be little that can be done about the current devices compromised by Meris, it is important that manufacturers do everything in their power to reduce the chances of such an event occurring. Commodity hardware such as routers, which are public-facing and typically remain unmonitored for long periods of time, should not require manual intervention from customers in order to apply critical security patches. The reliance on consumers to correct the mistakes of product vendors is a fault that has easily caused millions of dollars in damages in regards to interruptions caused by DDoS attacks. Possible preventative countermeasures for the future include having routers registered, rolling out over-the-air firmware updates to patch vulnerabilities, and educating the market on the importance of staying up-to-date.

